Security
Rethinking Entry-Level Developers in an AI-Driven World
In this second installment of our four-part series on artificial intelligence’s role in reshaping software development teams, we focus on entry-level developers. The rapid adoption of AI has led to predictions of reduced demand for junior roles, traditionally tasked with routine coding duties. However, this narrative overlooks strategic opportunities for organizations. Forward-thinking companies are redefining…
Read MoreMaximizing Developer Productivity: AI as a Strategic Skill Amplifier
Launching our four-part series exploring artificial intelligence’s transformative impact on software development, this article reveals how incorporating AI into development processes transcends simple task automation. AI fundamentally redefines productivity and innovation potential, empowering developers by amplifying their capabilities. Rather than replacing professionals, AI strategically enhances efficiency, freeing developers to concentrate on high-value tasks, creativity, and…
Read MoreCrafting Human-Like Real-Time Voice Chatbots: A Comprehensive Developer’s Guide
Introduction Human conversations are fluid, spontaneous, and laden with subtle social cues. By contrast, AI voice chatbots often sound overly polished and scripted, risking a user perception of “robotic” interactions. This guide outlines approaches for developers to bridge that gap, leveraging the natural “imperfections” of human speech—such as filler words, interruptions, and emotional inflections—to…
Read MoreAI Decision-Making in Business: A Practical Guide for Leaders
Artificial intelligence (AI) has the potential to transform how companies operate, creating opportunities for faster decisions, cost savings, and new sources of growth. At the same time, AI can feel intimidating, especially when it comes to “agentic” systems—tools that can make decisions on their own or with minimal human supervision. This guide aims to show…
Read MoreOvatioComply: Securing Enterprise AI While Enhancing Compliance
OvatioComply: Securing Enterprise AI While Enhancing Compliance When we designed OvatioComply, we focused on a simple truth: enterprises shouldn’t have to choose between AI innovation and regulatory compliance. More importantly, we recognized that AI could strengthen existing compliance and audit processes rather than complicate them. Financial analysts shouldn’t hesitate before using AI to detect fraud…
Read MoreOvatioIQ: Transform Your Organization’s Knowledge into Strategic Insights
In today’s fast-paced business environment, the true value of an organization’s information lies not just in storing documents, but in understanding their interconnections and extracting actionable insights. OvatioIQ is a groundbreaking knowledge management platform that transforms how organizations discover, access, and leverage their collective knowledge through intelligent conversations and visual insights. From Information Silos to…
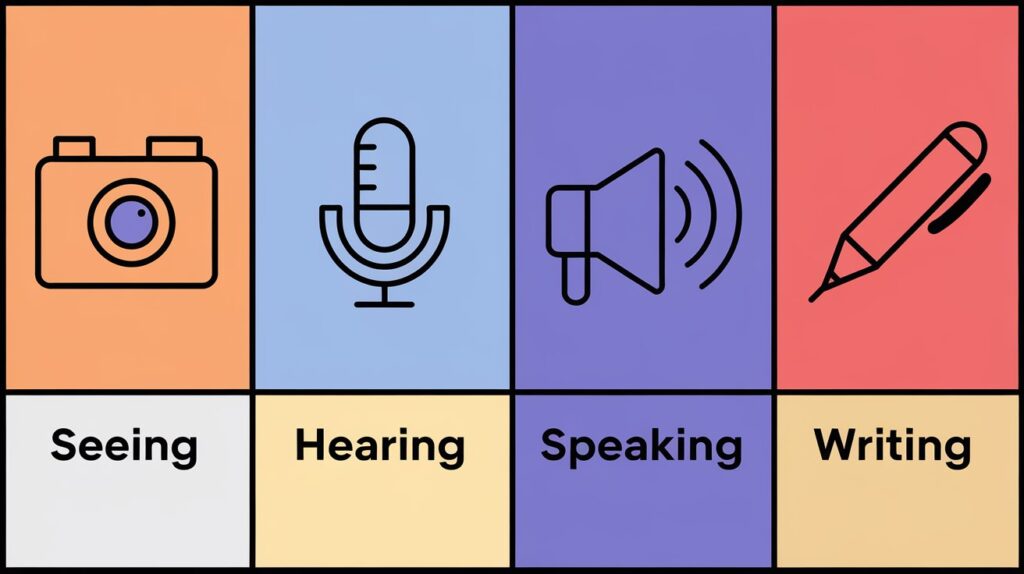
Read MoreAI Agents: The Power of Digital Senses in Business Automation
The artificial intelligence landscape has reached a pivotal moment. AI agents have evolved beyond simple automation tools, gaining abilities that were once uniquely human: seeing, hearing, speaking, writing, and reasoning. This convergence of capabilities has transformed AI agents from basic automation tools into sophisticated digital workers that can truly understand and interact with their environment.…
Read MoreLeveraging AI for Legacy System Integration: Unlocking Value in the Modern Enterprise
In today’s rapidly evolving digital landscape, many enterprises find themselves at a crossroads between legacy systems and modern technology demands. This article explores how artificial intelligence (AI) can be leveraged to create APIs for closed systems, offering a strategic solution that balances innovation with existing investments. This approach presents a compelling opportunity to drive digital…
Read MoreBalancing Innovation and Practicality in AI Projects: A Guide for IT Leaders
As artificial intelligence (AI) continues to evolve at a rapid pace, IT leaders face the challenge of harnessing its innovative potential while ensuring practical, value-driven implementations. Striking the right balance between cutting-edge AI capabilities and practical business solutions is crucial for successful AI adoption. This article provides guidance for IT leaders on how to navigate…
Read MoreVerkada and Exchange Attacks: Could you fall victim, too?
Who is Verkada? What happened? Verkada is an IP camera company. They provide cloud-based software that stores videos taken from their customers’ premises. Recently, they were hacked because a username and password with admin access had been exposed. Someone harvested this, put it on the internet, and took advantage of the credentials. This type of…
Read More